Security Whitepaper
CTICloud Security Whitepaper
Legal Statement
CTICloud reminds you to carefully read and fully understand each clause of this legal statement (hereinafter referred to as "this Statement") before reading or using the "CTICloud Contact Center Security Whitepaper" (hereinafter referred to as "this Document"). If you read or use this Document, your reading or use will be deemed as your acknowledgment of all contents of this Statement.
-
Authorization and Confidentiality Obligations
- You should download and obtain this Document through the CTICloud website or other authorized channels provided by CTICloud, and may only use it for your own lawful and compliant business activities
- The contents of this Document are considered confidential information of CTICloud, and you should strictly comply with confidentiality obligations
- Without prior written consent from CTICloud, you may not disclose the contents of this Document to any third party or provide it for any third party to use
-
Copyright Protection
- Without prior written permission from CTICloud, no organization, company or individual may excerpt, translate, copy part or all of the contents of this Document, or disseminate or publicize it in any way or through any channel
-
Content Updates
- Due to product version upgrades, adjustments or other reasons, the contents of this Document may change
- CTICloud reserves the right to modify the contents of this Document without any notice or prompt, and releases updated versions from time to time through CTICloud authorized channels
- You should pay attention to version changes of the document in real time, and download and obtain the latest version through CTICloud authorized channels
-
Disclaimer
- This Document is only provided as a reference guide for users to use CTICloud products and services. CTICloud provides this Document with products and services in their "as is", "with defects" and "current functionality" state
- CTICloud makes its best efforts to provide corresponding introductions and operation guidelines based on existing technology, but makes no express or implied warranties regarding the accuracy, completeness, applicability, reliability, etc. of the contents of this Document
- CTICloud shall not bear any legal liability for any errors or economic losses of any organization, company or individual due to downloading, using or relying on this Document
- Under no circumstances shall CTICloud be liable for any indirect, consequential, punitive, incidental, special or criminal damages, including loss of profits suffered by users using or relying on this Document (even if CTICloud has been informed of the possibility of such losses)
-
Intellectual Property Rights
- All contents in this Document, including but not limited to images, architectural designs, page layouts, and text descriptions, are intellectual property owned by CTICloud and/or its affiliates in accordance with law, including but not limited to trademark rights, patent rights, copyrights, and trade secrets
- Without written consent from CTICloud and/or its affiliates, no one may use, modify, copy, publicly disseminate, change, distribute, issue or publicly publish CTICloud websites, product programs or contents without authorization
-
Feedback
- If you find any errors in this Document, please contact CTICloud directly
Overview
As a well-known cloud service provider in China, since its establishment and operation in 2006, CTICloud's platform has been running stably with zero failures, zero risks, and zero security incidents, fully ensuring the information security and communication reliability of customers on the platform, and has been unanimously recognized by customers.
Data security and user privacy are CTICloud's most important principles. CTICloud is committed to building a public, open and secure cloud contact center platform. Through technological innovation, CTICloud continuously improves computing power and economies of scale, turning the cloud contact center into a true infrastructure.
CTICloud is dedicated to providing customers with stable, reliable, secure and compliant cloud computing infrastructure services, helping customers protect the confidentiality, integrity and availability of their systems and data.
Whitepaper Contents
This whitepaper comprehensively introduces the security system of CTICloud Contact Center, including the following core contents:
- Shared Responsibility Model - Clarifies the security responsibility boundaries between CTICloud and customers
- Security Compliance and Certifications - Demonstrates authoritative security qualifications obtained
- Infrastructure Architecture - Introduces cross-region, cross-cloud high-availability infrastructure
- Security Technology Architecture - Details the multi-layered security protection system
- Data Security Protection - Explains security mechanisms throughout the data lifecycle
- Monitoring and Emergency Response - Describes the 7×24 security operations system
Chapter 1: Shared Security Responsibility
For customer applications based on CTICloud Contact Center, security responsibility is shared by both parties: CTICloud ensures the security of the cloud contact center platform itself and provides security capabilities to customers on the cloud; customers are responsible for the security of their own use of CTICloud Contact Center services and application systems built based on APIs.
1.1 CTICloud's Security Responsibilities
CTICloud is responsible for the security of infrastructure and cloud platforms, specifically including:
Infrastructure Security
- Public cloud resources deployed across regions and multiple availability zones
- IDC data centers across regions and multiple locations
- CTICloud backbone transmission network
- Physical and hardware security of computing, storage and network equipment
Cloud Platform Security
- Identity management and access control of the cloud contact center platform
- Platform monitoring and operations
- Patch management for operating systems and databases
- Network access control and DDoS protection
- Disaster recovery and business continuity
Security Compliance and Auditing
- Timely discovery and repair of security vulnerabilities in the cloud contact center platform (repair process does not affect customer business availability)
- Cooperation with external third-party independent security supervision and audit institutions to conduct security compliance and audit assessments of the cloud contact center platform
Security Capabilities Provided to Customers
- Cloud data centers distributed across multiple regions and availability zones, and multi-line BGP access networks
- Account security management capabilities (account password security policies, secure API verification mechanisms, IP address access restrictions, multi-factor authentication, group authorization, fine-grained authorization, temporary authorization, etc.)
- Security monitoring and operations capabilities, including security audit means
- Data encryption means
1.2 Customer's Security Responsibilities
Customers should perform security configuration management on cloud contact center platform accounts to ensure the basic security and data security of cloud businesses.
Account Security Management
- Protect cloud contact center account authentication credentials (for example, enable multi-factor authentication)
- Follow the principle of least privilege in account settings
- Implement separation of duties through role-based and permission-based means
- Use the cloud contact center's operation audit service to record management console operations and API call logs
Data Security Management
- Use CTICloud Contact Center's data encryption capabilities
- Encrypt or hide sensitive data and properly manage encryption keys
- Use data hiding and desensitization capabilities to protect sensitive information
Application Security
- Configure and use CTICloud Contact Center products in a secure manner
- Build your own applications and businesses in a secure and controllable manner through API calls
- Ensure the security of your own applications and businesses
1.3 Advantages of Shared Responsibility Model
Under the shared responsibility model, CTICloud ensures platform-level security and provides security configuration and API interface security mechanisms. Based on more than 15 years of accumulated security operations and maintenance experience, CTICloud provides customers with a high-availability, high-security cloud contact center platform, protects customer cloud business and application system data security, reduces customer concerns about security, and allows customers to focus more on core business development.
Chapter 2: Security Compliance and Certifications
CTICloud's security process mechanisms have been recognized by relevant authoritative institutions at home and abroad. We integrate our long-term experience in combating Internet security threats into the security protection of the cloud contact center platform, integrate numerous compliance standards into the compliance internal control management and product design of the cloud contact center platform, and extensively participate in the formulation of various cloud computing service-related standards and contribute best practices, verifying how CTICloud complies with standards through independent third parties.
2.1 International Certifications
ISO 27001 - Information Security Management System
ISO 27001 is a widely adopted global information security standard. CTICloud is one of the cloud computing service providers in China that has passed this certification. This certification proves CTICloud Contact Center platform's security responsibilities in various aspects such as data security, network security, communication security, and operational security.
ISO 9001 - Quality Management System
ISO 9001 is used to demonstrate that an organization has the capability to provide products that meet user requirements and applicable regulatory requirements, and is an authoritative certification in the field of quality management.
ISO 20000 - IT Service Management
ISO 20000 is the first internationally recognized IT service management standard. CTICloud has passed the new version ISO/IEC 20000-1:2018 certification, which means that CTICloud has established standard service processes and strictly implements them, standardizes cloud platform services, improves efficiency and reduces overall IT risks.
ISO 14001 - Environmental Management System
CTICloud has passed GB/T 24001-2016/ISO 14001:2015 certification, proving that it has reached international standards in environmental management, can ensure that the control of various pollutants in various processes, products and activities of the enterprise meets relevant requirements, and has established effective environmental management capabilities and security protection capabilities.
2.2 Domestic Authoritative Certifications
Public Security Bureau Network Security Level Protection 2.0 Level 3 Certification
CTICloud Contact Center platform has obtained the Public Security Bureau's "National Information System Security Level Protection" non-banking institution's highest level - Level 3 filing certification and successfully passed the assessment. This certification level is a "regulatory level", and the security of the cloud contact center platform was rated as "good".
This certification represents that CTICloud has been supervised and recognized by the Public Security Bureau in information security and systematic standardized management, marking that CTICloud Contact Center system security has reached the highest level in the industry and can provide customers with high-security services.
Trusted Cloud Certification
Trusted Cloud Assessment is the cloud computing service and software assessment brand under the China Academy of Information and Communications Technology, and is also my country's professional assessment system for cloud computing services and software.
The core goal of trusted cloud service assessment is to establish an assessment system for cloud service providers, provide support for users to choose secure and trustworthy cloud service providers, promote healthy and innovative development of my country's cloud computing market, improve service quality and integrity levels, gradually establish a trust system for the cloud computing industry, and is widely accepted and trusted by the industry.
CTICloud is the first cloud contact center vendor in China to pass trusted cloud certification.
2.3 Regulatory Compliance
CTICloud actively fulfills laws and regulations and implements relevant policies, promoting enterprises to accelerate digital and intelligent transformation using cloud contact center technology.
Network Security Law Compliance
In accordance with the relevant requirements of the "Network Security Law", establish information service-related security management processes and systems within the enterprise, and ensure internal implementation of compliance requirements through systematic means.
Level Protection 2.0 Compliance
In accordance with the network security level protection system, continuously improve the proactive defense, dynamic defense, overall prevention and control, and precise protection capabilities of cloud contact center services. CTICloud became one of the first cloud contact center service providers to pass the Level Protection 2.0 formal standard assessment in November 2019, after the Level Protection 2.0 series of standards were officially released in May 2019.
2.4 Personal Information Protection
For a long time, CTICloud has been committed to protecting the personal information of every customer, ensuring that customers have ownership and control over all personal information provided to CTICloud.
Personal Information Protection System
- Establish a professional security management team
- Continuously optimize privacy policies and user rights protection
- Establish an overall internal data security management system
- Implement core technologies for data security protection
- Provide safe and reliable protection capabilities for the entire lifecycle of user personal information
Certification Proof
Through certifications from a large number of authoritative institutions such as ISO 27001, Level 3 Protection certification, and Trusted Cloud certification, prove personal information protection capabilities and data security protection capabilities. CTICloud will continue to build an overall personal information protection management system.
2.5 Transparency
CTICloud has long been committed to providing customers with transparency about cloud service providers through multiple channels. Customers can request information about CTICloud's qualifications, explanatory reports, etc. through emails and account managers. For reasonable customer requests, CTICloud will respond promptly, further eliminating customer doubts about CTICloud's internal "black box".
Chapter 3: Infrastructure Architecture
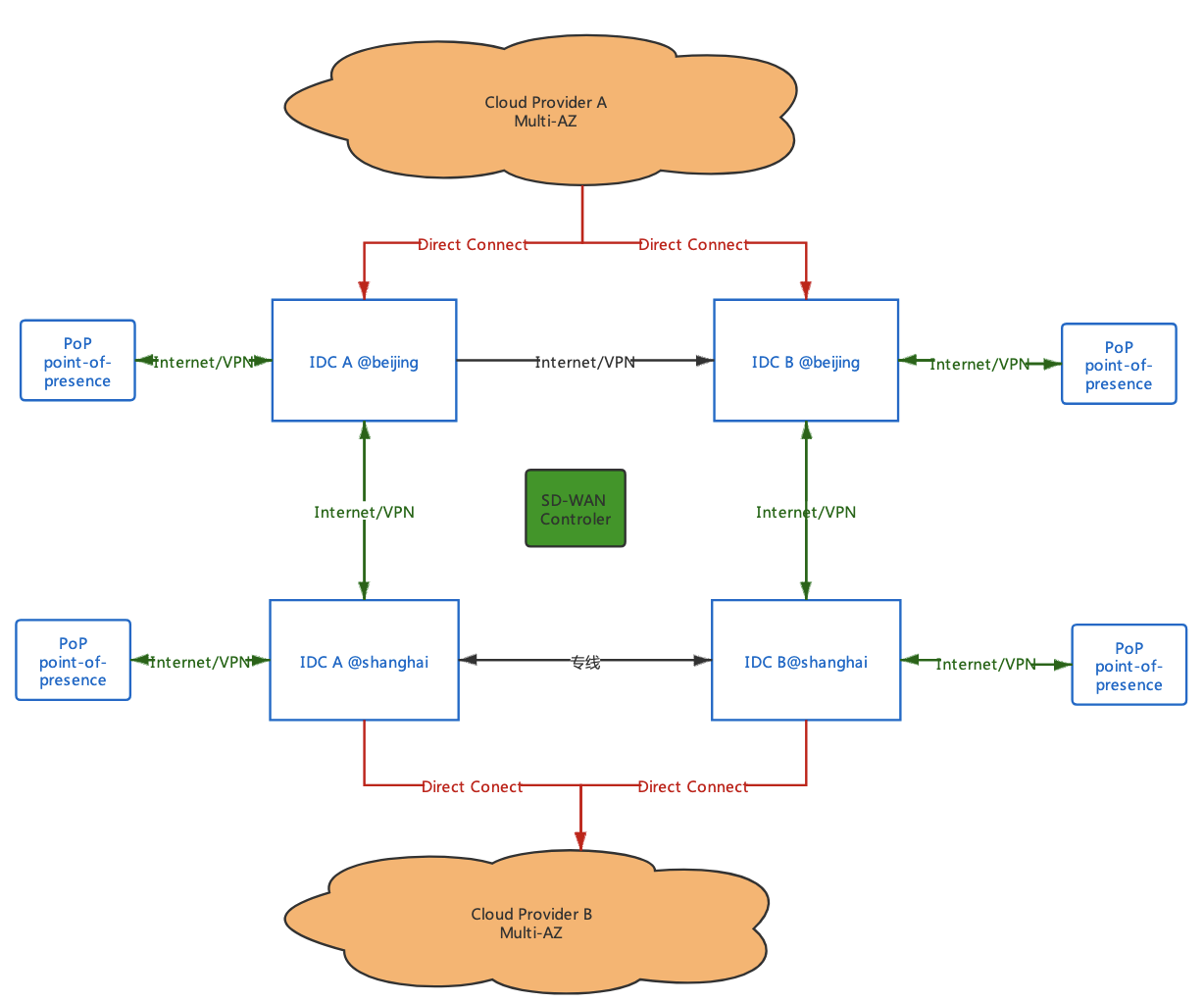
3.1 Cross-Region, Cross-Cloud Active-Active Infrastructure
CTICloud provides customers with an industry-leading cross-region, cross-cloud service provider dual-cloud contact center platform architecture, ensuring business high availability and continuity.
Multi-Cloud Strategy
- The cloud contact center platform runs simultaneously on two leading cloud platform service providers
- Each core data center is connected to two cloud platforms via fiber optics, linking two different cloud platform service providers
- If any cloud platform service provider experiences problems, business can be quickly switched to another cloud platform
High Availability Architecture
- Through network layer decoupling and IaaS layer decoupling, infrastructure load balancing and high availability are achieved
- When any data center or cloud platform service provider becomes unavailable, business can be quickly switched to other infrastructure
- Business stability does not depend on any single data center or cloud service provider
Architecture Topology
Cross-Region Dual-Cloud Four Core Data Centers Infrastructure Topology:
CTICloud Overall Platform Architecture Diagram:
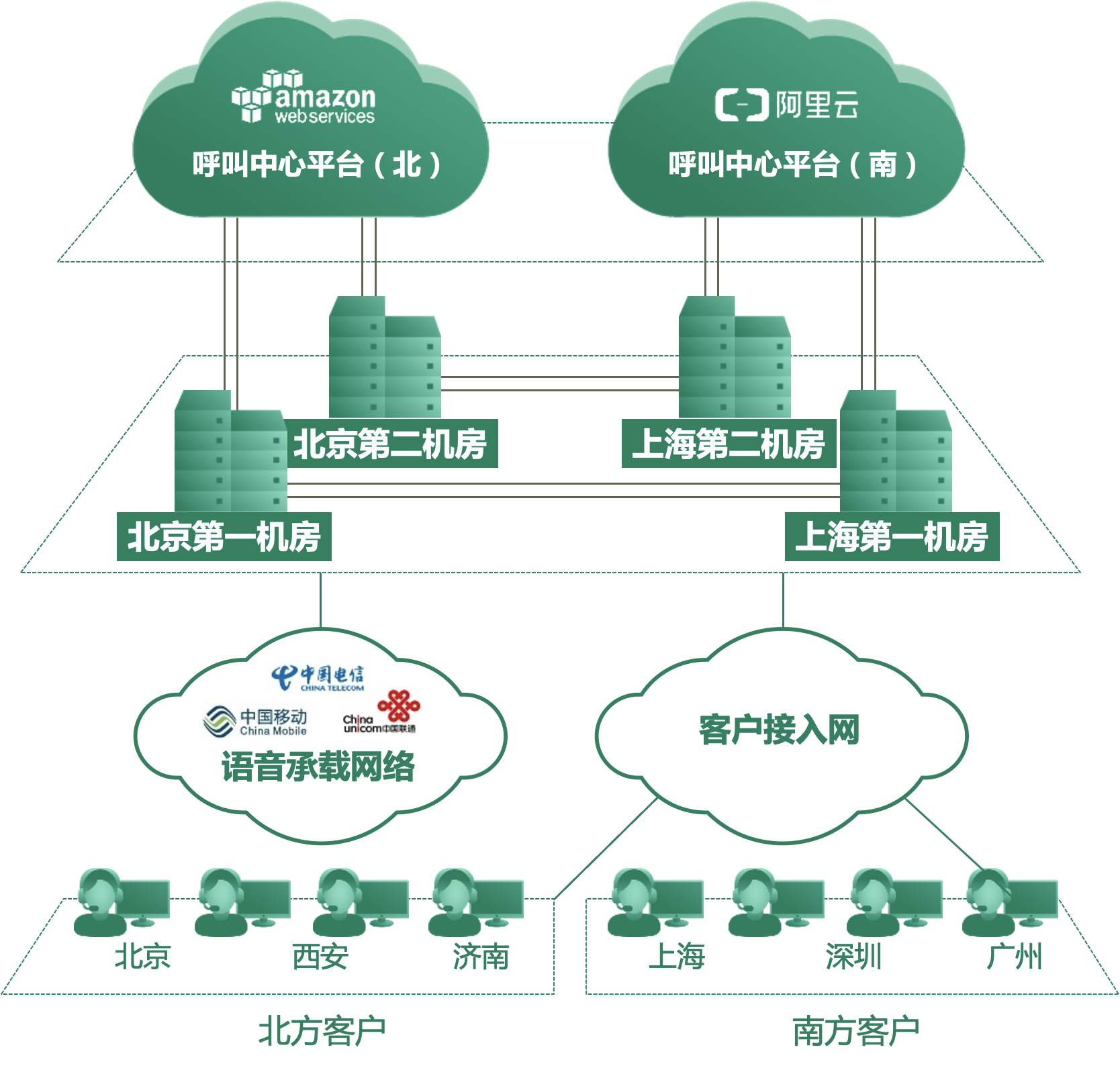
3.2 SD-WAN Core Network Architecture
CTICloud adopts an SD-WAN-based core data center Full-Mesh connection networking structure to achieve network high availability and intelligent scheduling.
SD-WAN Technical Advantages
- Control and Data Separation: Achieves separation between network hardware and lines from the control platform
- Full-Mesh Topology: Achieves full-mesh connections between all nodes in the core network
- Real-time Monitoring: Has the capability to detect network status in real time
- Millisecond-level Switching: When any node fails, automatic switching can be achieved at the millisecond level
- Traffic Scheduling: While operating stably at large scale, achieves centralized and flexible traffic scheduling
Multi-Data Center Disaster Recovery
- Two core data centers each have been built in Beijing and Shanghai, totaling 4 core data centers
- The 4 data centers are connected through SD-WAN, forming a Full-Mesh network
- When any data center experiences problems, business can be quickly switched to other core data centers
- Ensures cross-region high availability between core data centers
3.3 Multiple Access Methods
CTICloud Contact Center supports multiple access methods to meet the connection needs of different customers.
Internet Access
For customers accessing via the Internet:
- Multiple cloud service provider Internet connections
- IDC data center Internet access backup
- Ensures high availability of Internet access
Dedicated Line Access
For dedicated line access customers:
- Customers can pull local or long-distance dedicated lines directly connected to different CTICloud data centers
- Supports direct connections to data centers in different regions
- Achieves high-availability (cross-region) dedicated line access
3.4 Infrastructure Inventory
| Region | City | Number of Data Centers | Data Center Partners |
|---|---|---|---|
| North China | Beijing | 2 | Sinnet Technology Co., Ltd. GDS Digital System Co., Ltd. |
| East China | Shanghai | 2 | GDS Services Limited 21Vianet Group, Inc. |
| South China | Guangzhou | 1 | Guangzhou Visu Information Technology Co., Ltd. |
| Shenzhen | 1 | Shenzhen Xialong Futian Data Center |
Chapter 4: Security Technology Architecture
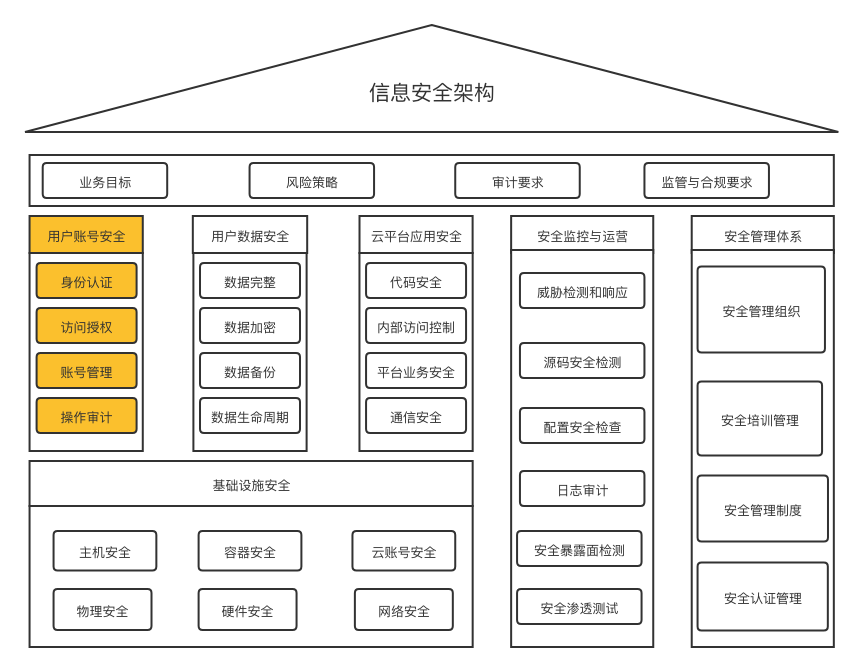
CTICloud Contact Center security architecture adopts a multi-layered, three-dimensional security protection system:
4.1 Architecture Layers
Horizontal Layers
- Infrastructure Security Layer: Includes physical security, hardware security, host security, network security
- Cloud Platform Security Layer: Includes user account security, user data security, application security
Vertical Integration
- Security Monitoring and Operations: A comprehensive security monitoring and operations system that spans both horizontal layers
4.2 Security Capability Description
Platform Intrinsic Security
User data security, application security, and security monitoring and operations in the cloud platform security are managed by CTICloud's internal security management and operations, without direct customer perception.
Infrastructure Security
At the infrastructure security level including physical security, hardware security, host security, and container security, customers can enjoy the high security level capabilities of CTICloud cloud services without any settings.
User-Configurable Security
The user cloud account security layer includes security capabilities and security guarantees provided by the cloud contact center platform to customers:
- Default Protection: Some capabilities (such as tenant isolation) are default protections of the product itself
- Optional Configuration: Some capabilities (such as data encryption) require customers to enable and correctly configure the capabilities provided by the product
Chapter 5: Infrastructure Security
5.1 Physical Security
Data Center Standards
The data centers selected by CTICloud are built with high standards, providing:
- High customization
- High availability
- High security
- High disaster recovery
- Low energy consumption
Cloud Platform Partners
CTICloud has selected two cloud computing service vendors that are in absolute leading positions in the international and domestic markets. They follow strict management processes in physical security, authorization management, etc., ensuring the security of the infrastructure environment.
Network Isolation
CTICloud has physically isolated production networks from non-production networks. Non-production networks cannot directly access any servers or network equipment in production networks.
5.2 Bastion Host Security
Bastion Host Functions
Bastion host service is a security product for managing and controlling IT operation personnel and operation behaviors, mainly solving the following problems:
- Multiple people using the same host account to log in to the host, making it difficult to locate responsible persons
- Complex host password management with serious password leaks
- Opaque operations of operation personnel, unauthorized access leading to data leaks
- Strict legal and regulatory requirements, prominent cloud security operation and maintenance management risks
Bastion Host Deployment
- CTICloud has deployed bastion hosts at production network boundaries
- Operation personnel in the office network can only enter the production network for operation and maintenance through bastion hosts
- When logging in to bastion hosts, operation personnel use domain account passwords plus dynamic passwords for multi-factor authentication
- Bastion hosts use high-strength encryption algorithms to ensure the confidentiality and integrity of data transmission in operation and maintenance channels
Core Capabilities
Bastion host services integrate the following functions:
- Operation and maintenance identity authentication
- Account control
- System operation auditing
- Based on protocol forward proxy implementation
- Full recording of SSH protocol data flow through forward proxy
- Video playback through protocol data flow reassembly to achieve operation and maintenance operation auditing
5.3 Network Security
Organizational Guarantee
Designate specialized departments and personnel responsible for planning, construction, management and maintenance of network security systems.
Security Domain Division
- Divide networks and information systems into security domains and establish isolation protection mechanisms
- Establish access control mechanisms between security domains to prevent unauthorized illegal access
- Specially divide and isolate production networks and office networks
Network Management
- Deploy network management system to manage network resources and equipment
- Monitor the operating status of network systems
- Reduce security risks from network failures
Redundancy Design
Critical communication lines and network equipment provide redundancy design to prevent communication service interruptions caused by single point failures of critical lines and equipment.
Multi-layered Protection
At the boundaries of security domains, comprehensively deploy network security access measures:
- Firewalls
- Intrusion detection
- VPN
- Establish multi-layered, three-dimensional network security protection system
5.4 Host Security
CTICloud Contact Center platform uses mainstream third-party vendor security products to implement host security management:
Host Service Detection Engine
- Provides fast and convenient host service asset detection functions
- Quickly and accurately collects host service asset information
- Users can customize port detection groups for quick detection of common services
- Relies on built-in fingerprint libraries to achieve accurate and fast host service asset identification
- Provides domain name reverse resolution functions to assist users in correlating host service assets and web assets
Domain Name Detection
- Supports analysis of domain name assets from multiple dimensions, such as search engines, HTTPS certificates, Passive DNS, domain transfer vulnerabilities, etc.
- Combined with built-in dictionaries more suitable for domestic common naming habits, achieves comprehensive subdomain discovery
- Built-in domain name guessing dictionary suitable for Chinese common naming habits
- Quickly collects subdomain asset information through detection engine algorithms
- Performs correlated queries of domain name information through cloud service interfaces from search engines, HTTPS certificates and DNS resolution records
- Automatically detects web application status under domain names
- Supports DNS domain transfer vulnerability detection
- Comprehensively masters enterprise domain name asset information through regular scanning
Comprehensive Web Detection
- Uses comprehensive web detection engine to cope with complex and diverse web application architectures
- Can identify and analyze pages based on target URLs, selecting ordinary crawlers or browser crawlers based on page types
- Strives to comprehensively collect target site page information
- For Web 2.0 single-page applications, browser crawlers simulate local rendering and parsing processes of real browsers
- Ensures comprehensive and accurate web site information collection
- Users can customize request methods and URL keywords to avoid crawler operations causing data errors
- Supports multiple login methods, including HTTP basic authentication, Cookie/Session authentication, Token authentication and certificate authentication, etc.
- Achieves web application login scanning
Vulnerability Remediation
- Security patches are the most basic and effective way to deal with vulnerability risks
- CTICloud provides full lifecycle security vulnerability management, covering development, distribution and operation stages
- For enterprises, through professional patch collection, testing, backup and distribution processes, effectively manage patches and reduce the risk of patches themselves becoming new vulnerabilities
Intrusion Detection
- CTICloud Contact Center platform uses mainstream third-party vendor security products
- Through installing security center agents on hosts, achieves linkage with cloud security centers
- Provides real-time intrusion detection security capabilities
5.5 Application Security Protection
CTICloud Contact Center uses mature third-party security vendor-provided Web Application Firewall (WAF) services.
WAF Protection Capabilities
- Defends against SQL injection
- Defends against XSS cross-site scripting
- Defends against common web server plugin vulnerabilities
- Defends against trojan uploads
- Defends against unauthorized access to core resources
- Defends against OWASP common web attacks
- Filters massive malicious access
- Prevents website asset data leaks
- Ensures security and availability of website applications
Chapter 6: Identity Verification and Access Control
6.1 Identity Management
CTICloud uses identity authentication systems to manage account lifecycles for internal users including regular employees, interns, outsourcing, and partners.
Account Management Principles
- One Person One Account: All users are allocated and use accounts according to this principle
- Separation of Public and Private Data: Clearly distinguish between company data and personal data
- Unified Management: Unified login management, account password management and access control for accounts
- No Sharing: Once accounts are allocated, account sharing is not allowed
Account Recovery Mechanism
Once internal users leave, transfer positions or work content changes, all account resources they use or manage must be promptly recovered or transferred.
6.2 Password Management
Password Policy
- Follow the principle of one person one account, each account has a clear holder
- Password policies are centrally distributed to all users
- Mandatory requirements to set passwords that meet password length and complexity requirements
- Regularly change passwords and cannot be the same as the previous password
Multiple Authentication Methods
CTICloud internal systems support multiple authentication login methods:
- Account password login
- One-time password login
- Digital certificate login
6.3 Permission Management
Permission Management System
CTICloud rationally allocates permissions according to business needs, and uniformly manages permissions according to the following levels:
- Permissions
- Roles
- User groups
- Departments
- Users
Permission Lifecycle
Each internal user implements the following through the permission management system:
- Permission application
- Permission use
- Permission recovery
Hierarchical Approval Mechanism
To strengthen internal system permission usage management and reduce permission usage risks:
- Permissions and roles are set to different levels according to risk
- Different levels of application approval mechanisms are implemented according to levels
6.4 User Administrator Security Requirements
Clear security requirements for user administrators:
-
Multi-Factor Authentication: User administrators should centrally set multi-factor authentication policies for accounts
-
Password Complexity Policy: User administrators should centrally set password complexity policies for accounts
- Password length at least 10 characters
- Include at least 3 of 4 categories: numbers, lowercase letters, uppercase letters and special symbols
-
Login Error Lockout Policy: User administrators should centrally enable login error count lockout policies for accounts
- Maximum 5 login attempts with wrong password within one hour
-
Password Expiration Policy: User administrators should centrally enable password expiration policies for accounts
- Password expiration period generally no more than 90 days, maximum no more than 180 days
- After password expiration, user login should be restricted
-
IP Whitelist Restriction: Add IP whitelist login security restrictions for high-privilege accounts
- Recommended to only allow office network access
-
Key Management Specifications:
- Do not create keys for main accounts
- Do not create keys for console users
- Key usage time cannot exceed half a year
-
Authorization Process Management: Account opening authorization management must go through workflow tickets
6.5 Regular Employee Security Requirements
Clear security requirements for regular employees:
-
Ticket Approval System: Public cloud platform account opening, creating AK/SK, permission application or change should submit ticket for approval
-
Sensitive Information Protection: Sensitive information such as AK/SK keys cannot be hardcoded in source code
-
Account Independence: One person one account, account sharing or use is not allowed
Chapter 7: Cloud Product Security Lifecycle Management (SPLC)
The goal of Secure Product Lifecycle (SPLC) is to integrate security into the entire product development lifecycle. SPLC checks at every stage including product architecture review, development, testing review, and emergency response. Each node has a complete security review mechanism to ensure that the security performance of products can meet strict cloud requirements, thereby effectively improving the security capabilities of cloud products and reducing security risks.
7.1 Six Stages of SPLC
Stage 1: Product Initiation
In the product initiation stage, security architects and product teams jointly based on business content, business processes, and technical frameworks:
- Establish FRD (Functional Requirements Document)
- Draw detailed architecture diagrams
Stage 2: Security Architecture Review
In the security architecture review stage, security architects based on FRD and architecture diagrams:
- Conduct targeted security architecture assessments of products
- Create product threat modeling
- Synthesize security solutions from "Security Baseline Requirements" and threat modeling
- Confirm all "Security Requirements" for the product with the product team
Stage 3: Secure Development
In the secure development stage, product teams follow "Security Requirements":
- Follow secure coding specifications in product development
- Implement relevant security functions and requirements of products
- Conduct self-assessment to confirm that all "Security Requirements" have been implemented
- Provide corresponding testing information (such as code implementation addresses, self-test result reports, etc.) to security engineers
- Prepare for the next stage of security testing review
Stage 4: Security Testing Review
In the security testing review stage, security engineers based on "Security Requirements":
- Conduct comprehensive security review of products including architecture, design, server environment, etc.
- Conduct code review and penetration testing of product code
- Security issues discovered at this stage will require product teams to perform security fixes and hardening
Stage 5: Application Release
In the application release stage:
- Only after passing security review and obtaining security approval can products be deployed to production environments through standard release systems
- Prevent products with security vulnerabilities from running in production environments
Stage 6: Emergency Response
In the emergency response stage, security emergency teams:
- Continuously monitor possible security issues of the cloud contact center platform
- Obtain security vulnerability information through external channels (such as ASRC, etc.) or internal channels (such as internal scanners, security self-testing, etc.)
- After discovering vulnerabilities, quickly rate security vulnerabilities
- Determine the urgency and repair schedule of security vulnerabilities
- Reasonably allocate resources to quickly and reasonably fix security vulnerabilities
- Ensure the security of user business and data
Chapter 8: Security Monitoring and Operations
8.1 Cloud Platform Security Monitoring
Security monitoring is a very important link. Detection is the basis for dynamic response and enhanced protection, and it is also a powerful tool for mandatorily implementing security policies. Through detecting and monitoring networks and information systems, discovering new threats and weaknesses, and making effective responses in a timely manner through cyclic feedback.
Monitoring Objectives
The main purposes of cloud platform security monitoring are:
- Timely discover security incidents of malicious attacks on the platform's own applications, hosts, networks and other resources
- After discovering security incidents, trigger the cloud contact center platform's internal emergency response process for proper handling
- Timely eliminate impacts
Monitoring Architecture
Security monitoring is mainly divided into three parts:
1. Log Collection
- Collect host logs, network logs, application layer and cloud product logs from the platform side
- Import into real-time computing platforms and offline computing platforms respectively
2. Anomaly Analysis and Detection
- In various computing platforms, process and analyze logs through security monitoring algorithm models
- Complete risk discovery and monitoring
3. Alert Display
- Once abnormal security incidents are discovered, display alerts on internal security monitoring platforms
- Notify security emergency personnel through DingTalk, SMS, Feishu, email notifications, etc.
- Ensure response and handling at the first time
8.2 Specific Monitoring Measures
-
CVE Vulnerability Detection
- Regularly use Wanxiang platform to conduct daily latest CVE-related vulnerability detection
- Continuously monitor intrusion detection logs daily to ensure system host security
-
Host Vulnerability Scanning
- Regularly conduct host vulnerability scanning work
- Ensure system host security
-
Penetration Testing
- Regularly conduct penetration testing work on various product line business systems
- Produce corresponding vulnerability reports
-
Vulnerability Scanning
- Regularly conduct vulnerability scanning work on various product line applications, hosts and network equipment
- Conduct security assessments to avoid known high-risk vulnerabilities
-
Code Security Review
- Regularly conduct code security review work
- Before system launch, detect code security issues through automated code auditing methods
8.3 Security Auditing
Cloud Platform Security Audit
Security Check Item | Specific Requirements | Execution Cycle |
|---|---|---|
Login Security Configuration |
| Monthly |
Access Control Security Configuration |
| Monthly |
AK/SK Security Check |
| Monthly |
User Permission Change Check |
| Monthly |
User Permission Rationality Check |
| Monthly |
Public Network Exposure Security Audit
Security Check Item | Execution Cycle |
|---|---|
| Monthly |
Bastion Host Security Audit
Audit Item | Security Check Item | Execution Cycle |
|---|---|---|
Security Configuration Check |
| Monthly |
Departed Personnel Account Check |
| Monthly |
User Permission Rationality Check |
| Monthly |
Access Control Check | Check whether bastion host is open to external networks | Monthly |
GitHub Security Audit
Audit Item | Security Check Item | Execution Cycle |
|---|---|---|
Security Configuration Check |
| Quarterly |
Sensitive Information Leak Detection |
| 7×24 monitoring |
8.4 Security Emergency Response
The emergency response of the cloud contact center platform refers to CTICloud's emergency handling of vulnerabilities and security incidents discovered through internal monitoring and reported externally.
Vulnerability Information Sources
Internal Monitoring
- The cloud platform side discovers possible security incidents through log collection and anomaly analysis detection methods
- Generate alerts
External Reporting
- ASRC emergency response center
- CVE vulnerability information disclosed by external open-source third-party components
- Threat intelligence information from third parties
Early Warning Mechanism
Regularly collect the latest early warning information, timely understand industry dynamics, latest vulnerabilities, latest risks, and coordinate local implementation of early warning information. Specific measures:
-
Security Incident Monitoring
- Through security detection equipment and security protection equipment, conduct security early warning monitoring and security analysis of various security incidents
- Issue security incident handling work orders to assist relevant departments in emergency handling of security incidents
-
Vulnerability Information Monitoring
- Real-time monitoring of vulnerability information disclosed by vulnerability response platforms, CNCERT, CNVD and other network security incident handling platforms and major security forums
- Implement dynamic security monitoring through screening and filtering relevant keywords
- Immediately launch information push and handling coordination when security vulnerabilities related to company systems are discovered
-
Weekly Report System
- Weekly compilation of security early warning reports and security knowledge from Internet Emergency Center (CNCERT), CNVD, CVE, antivirus vendors, operating system vendor announcements, alert information, and major credit websites
- Provide corresponding repair and rectification guidance
-
Tracking Implementation
- Weekly coordination with relevant staff to track and implement last week's security early warning information
- For early warning information, provide methods and solutions for checking vulnerabilities
- Conduct asset correlation and point out at-risk assets
Emergency Response Process
Once security incidents and vulnerabilities are discovered, CTICloud will conduct corresponding security emergency response:
Step 1: Investigation and Confirmation
- Investigate and confirm the authenticity of reported vulnerabilities and security incidents
Step 2: Launch Process
- Once confirmed, CTICloud Contact Center platform security personnel will launch the emergency response process
- Handle according to standard procedures
Penetration Testing Exercises
CTICloud periodically procures specialized third-party security vendors to conduct penetration testing exercises on the cloud contact center platform to verify:
- The effectiveness of CTICloud Contact Center platform's security protection system
- The smoothness of the security emergency response process
Chapter 9: User Data Security
User data security on the cloud contact center is the lifeline of users and is also the most important concrete manifestation of the overall security capabilities on the cloud contact center platform.
9.1 Data Ownership
CTICloud has clearly launched the "Data Protection Initiative" and publicly pledged and clarified:
Data uploaded, produced and processed by customers on the contact center cloud platform is absolutely owned by customers; CTICloud will not use this data for other purposes. CTICloud has the responsibility and obligation to help customers ensure the confidentiality, integrity and availability of their data.
9.2 Three Elements of Data Security (CIA)
Data security requirements can be summarized by the three basic elements of information security "CIA":
Confidentiality
- Specifically means that protected data can only be accessed by legal (or intended) users
- Main implementation methods include:
- Data access control
- Data leak prevention
- Data encryption
- Key management
Integrity
- Ensures that only legal (or intended) users can modify data
- Main implementation methods:
- Implemented through access control
- Ensuring user data integrity through verification algorithms in data transmission and storage
Availability
- Data availability is mainly reflected in:
- Overall security capabilities of the cloud environment
- Disaster recovery capabilities
- Reliability
- Normal operation guarantee of various related systems on the cloud (storage systems, network paths, identity verification mechanisms and permission verification mechanisms, etc.)
CTICloud's cloud data security capabilities can help users prevent data leaks and meet compliance requirements such as personal information protection and Level Protection 2.0.
9.3 Data Classification
Data Discovery and Detection
The first step in data classification is to discover and detect sensitive information in data, such as personal verification information.
Data Classification and Grading
The second step in data classification is to classify and grade data based on sensitive information in data, according to user usage scenarios, compliance needs and security requirements, thereby achieving the purpose of understanding data assets and subsequent targeted protection.
9.4 Sensitive Data Protection
CTICloud Contact Center platform treats customer phone numbers, usernames, recordings and other information as sensitive data, providing various data protection functions:
- Phone number encryption
- Phone number partial hiding
- Recording file name desensitization
- Recording file encryption
Customers can choose to enable such protection functions as needed.
9.5 Data Leak Prevention
User data leak prevention is mainly reflected in the completeness of data permission control and monitoring and detection capabilities during data use. To prevent data leaks, effective control of cloud contact center user permissions must first be achieved.
Access Security Control Policy
CTICloud Contact Center provides effective data access security control policies. The system contains strict identity authentication and access control policies that can effectively avoid unauthorized access issues:
-
IP Whitelist Access Policy
- System supports configuring IP whitelist access policies to ensure system and data security
-
HTTPS Encrypted Transmission
- System uses HTTPS secure communication protocol for encrypted transmission to prevent network layer information leaks
-
Multi-level Verification Mechanism
- In business inquiry and handling processes, requires users to input different verification information according to different security level requirements
- Can only proceed to the next step after verification
-
Internal Core Area Storage
- System is only responsible for information transmission (encrypted or unencrypted) and specific display work
- Important data information is stored in internal core areas, ensuring security physically
-
Unified Authentication Integration
- Through unified authentication integration interface, achieves integration with user backend security authentication mechanisms
- Can only log in to system management backend after application in user system
-
Backend Permission Verification
- Has backend permission verification mechanism, unauthorized users cannot access
- System users are managed in layers and have flexible adjustment and fine-grained permission control
9.6 Data Integrity
Cloud Service Provider Guarantee
- In data transmission and storage, CTICloud Contact Center uses mainstream cloud service vendors (AWS, Alibaba Cloud, Tencent Cloud, etc.) to ensure data integrity and storage high availability
- Refer to cloud service vendor security documentation for details
Recording Storage Guarantee
- Call recordings are stored in cloud service provider platform object storage
- Provides high reliability guarantees:
- AWS: 11 nines (99.999999999%)
- Alibaba Cloud: 12 nines (99.9999999999%)
9.7 Link Encryption
CTICloud provides full-link encryption protection capabilities for data security, including Encryption in Transit and Encryption at Rest. At the same time, CTICloud Contact Center provides encryption services based on cloud service platform hardware encryption machines and SSL certificate services, providing users with complete data encryption solutions.
Transmission Encryption
1. SSL/TLS Protocol
- The cloud contact center platform provides SSL/TLS protocol to ensure data transmission security for user access (including reading and uploading) data
- For example, when users call cloud contact center API interfaces, HTTPS is used for data transmission
2. HTTPS Encryption Strength
- All cloud contact center products provide API access points supporting HTTPS for customers
- Provides up to 256-bit key transmission encryption strength
- Meets sensitive data encrypted transmission needs
3. Dedicated Line Access
- CTICloud also provides dedicated line access methods for customers to ensure transmission link encryption functions on networks
- Can securely and reliably connect enterprise local IDC with CTICloud Contact Center platform through transmission link encryption channels
Storage Encryption
1. Recording Encryption Service
- CTICloud Contact Center provides recording disk storage encryption capabilities to users
- Uniformly uses Key Management Service (KMS) for key management
- Storage encryption provides 256-bit key storage encryption strength (AES256)
- Meets sensitive data encrypted storage needs
2. Envelope Encryption Mechanism
Encryption keys are divided into two layers, implementing data encryption through envelope encryption mechanism:
- First Layer: Customer Master Key (CMK)
- Second Layer: Data Encryption Key (DEK)
Where CMK performs encryption and decryption operations and protection for DEK, and DEK performs encryption and decryption operations and protection for actual data.
Encryption Process:
- When data is written to disk storage, cloud products write the data key ciphertext (encrypted using CMK through KMS) together with the ciphertext data (encrypted using DEK on the storage link by cloud products) to permanent storage media
- As the name implies, the "envelope" in envelope encryption refers to the conceptual packaging of data key ciphertext and data ciphertext in an "Envelope"
Decryption Process:
- When reading encrypted data, the data key ciphertext is also read together and decrypted before the data
- Only after the data key is decrypted can the ciphertext data be read normally
3. Key Protection
- Customer Master Key CMK is protected by the key management infrastructure provided by cloud service provider KMS
- Implements strong logical and physical security controls to prevent unauthorized access
- Cloud service provider's key management infrastructure complies with recommendations in NIST 800-57
- Uses cryptographic algorithms and Hardware Security Modules (HSMs) that meet compliance requirements
- Throughout the envelope encryption process, CMK plaintext is never stored or used outside the HSM hosted by KMS
4. Recording Encryption Algorithm
- Encryption algorithm adopts envelope encryption principle, key data is encoded together with recording files
- Key data encoding adopts TLV format, optimized custom data length
- Encrypted recordings can be played, but the content is blank noise, only after decryption will there be recording content
Chapter 10: User Account Security Management
10.1 Account Password Authentication
Users can use their cloud contact center account (i.e., main account) to log in to the cloud contact center platform console and operate on configurations and data.
Password Policy Management
- Account password specifications and login security risk control policies of CTICloud Contact Center platform are uniformly managed by CTICloud
- Password policies for sub-users under main accounts can be set by customers themselves, including:
- Password character combination specifications
- Retry login attempts
- Password rotation period
10.2 Access Key (AK) Authentication
AK Identity Credentials
- Access Key (AK) is the identity credential for users to call CTICloud Contact Center platform APIs
- Used to authenticate user identity when users access CTICloud Contact Center platform resources through APIs
- API credentials are equivalent to login passwords, only with different usage scenarios:
- Access Key is used for programmatic calling of cloud service APIs
- Login password is used to log in to console
AK Components
Access Key consists of two parts:
- Access Key ID (AK ID): Used to identify users
- Secret Access Key (AK Secret): Used to verify the legality of user identity
AK Usage Process
- Users pass in AK ID when calling resources
- Use AK Secret to sign requests
AK Management
- Users can log in to CTICloud Contact Center platform console to manage Access Keys in enterprise settings
- Supported operations include: create, freeze, activate and delete
- Access Key is a long-term API access key
- It is recommended that users consider periodic rotation of Access Keys when using them
10.3 MFA Authentication
MFA (Multi-Factor Authentication) is a simple and effective best security practice method that can add an additional layer of security protection beyond username and password.
MFA Working Principle
After enabling MFA, when users log in to the cloud contact center platform, the system will require:
- First Security Factor: Enter username and password
- Second Security Factor: Enter variable verification code from MFA device
These multiple factors combined will provide higher security protection for user accounts.
Virtual MFA Devices
- Supports software-based virtual MFA devices
- Virtual MFA devices are applications that generate 6-digit authentication codes
- Follow Time-based One-Time Password (TOTP) standard
10.4 Operation Auditing
CTICloud Contact Center platform provides operation log management for users, recording user login and resource access operations under accounts.
Audit Log Contents
- Operator
- Operation time
- Source IP address
- Resource object
- Operation name
- Operation status
Audit Application Scenarios
Using all operation records saved in operation logs, users can achieve:
- Security analysis
- Intrusion detection
- Resource change tracking
- Compliance auditing
Compliance Auditing Support
To meet user compliance auditing needs, users often need to obtain detailed operation records of main accounts and their sub-users. Operation events recorded in operation logs can meet such compliance auditing needs.
Conclusion
CTICloud Contact Center security system is a multi-layered, three-dimensional comprehensive security protection system, covering comprehensive security guarantees from infrastructure to application levels. Through continuous technological innovation, strict security management and complete emergency response mechanisms, CTICloud is committed to providing customers with secure, stable and reliable cloud contact center services.
We will continue to uphold the principle of "security first", continuously optimize and improve the security system, and work together with customers to build a secure and trustworthy cloud communication environment.
Updated 17 days ago